SECURITY CERTIFIED
#1 IN THE WORLD

#Certified
Can a Simple Selfie Really Provide Security?
No, because 2D photos of most people are available all over the Internet. But FaceTec isn’t just a “selfie”; it’s a real-time 3D FaceScan that collects time-stamped, un-reusable Liveness data and creates a 3D FaceMap, which IS NOT publicly available online. FaceTec’s software isn’t fooled by photos, masks, or deepfakes, and ensures that the user is actually physically present.
FaceTec’s Liveness Detection AI must observe so many concurrent human traits that spoof artifacts are unable to recreate them all in real-time. For ongoing user re-verification, FaceTec’s 3D face matching compares a new Liveness-proven 3D FaceMap with the user’s previously-stored 3D FaceMap. If they match highly (1/125M FAR), the user can be granted access.
Try our $600,000 Spoof Bounty Program for yourself!
FaceTec’s Encrypted 3D FaceMaps:
- Can’t Be Phished From Users
- Aren’t a Biometric Honeypot
- Stop Credential Sharing
- Stop Botnet Attacks
- 1:1 Match at 1/125M FAR
- 1:N De-duplicate up to 1/1B FAR
- Match 2D Photos up to 1/2M FAR
- Provide Anonymous Age Checks
Want To Learn More?
Time-Stamped 3D Liveness = No Security Honeypot Risk
Two types of data are required for every face verification: 3D Face data for matching and real-time 3D Liveness data to prove the Face data was collected from a physically present person. 3D Liveness data is time-stamped, valid only for a few minutes, and can be deleted immediately. New 3D Liveness data must be collected for every subsequent 3D FaceScan.
FaceTec’s Customers don’t create security honeypot risk by storing 3D FaceMaps because they contain “face data” without the Liveness data required in a new 3D FaceScan session, so they cannot be re-used to spoof FaceTec’s 3D Liveness AI.
HOW FaceTec WORKS
As the camera’s view of the 3D user changes, it observes perspective distortion in the video. FaceTec’s AI processes the 100+ frames over two-to-three seconds and then interpolates that data into a 3D FaceMap from any .3MP+ 2D camera.
Certified Liveness Detection
We’ve devoted more time to anti-spoofing than anyone, ever. Over nearly a decade we’ve performed hundreds-of-millions of spoof attempts with every conceivable type of media and learned how to stop them. For more info see: www.Liveness.com
Attack Vectors include:
- 2D paper photos & digital images
- High resolution videos
- Paper masks with eye & mouth cutouts
- Hollywood masks, wax figures & lifelike dolls
- Photos or video frames animated into avatars
- Video projections on 3D heads
- Sleeping users with closed eyes
- Device Emulators & Virtual Camera programs
- Impostors, lookalikes & doppelgangers
- Hardware Video Injection adapters
Operating a Spoof Bounty Program since October 2019, and passing NIST/NVLAP Lab Level 1 & 2 PAD testing with 0% FAR years before that is proof that FaceTec is the biometric modality that is virtually impossible to fool using today’s media technology.

UR® Codes
What are UR Codes?
UR Codes contain digitally signed biometric data and enable privacy-preserving in-person and remote Identity Verification. Codeholders can prove, with high confidence, their legal identity, age, and right to access their accounts or privileges, both in-person and remotely. Because they store unique, signed face data, personal info, and legal identity data, UR Codes enable secure, low-cost, two-party identity verification at unlimited scale.
Learn More at URCodes.com and in the Intro to UR Codes.pdf
Look for the UR Code Seal for secure remote identity verification:
View the UR Code Developer Docs here
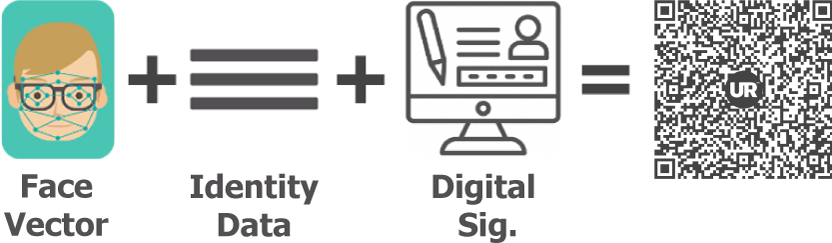
Immutably bind Anyone to their identity data from any Issuing Authority (DMV, school, employer, etc.).
Biometric Best Practices










- Demand 3D Liveness Detection backed by a Spoof Bounty Program. Without it, you cannot trust unsupervised users and will be put at risk by images on Facebook/Google/YouTube, and those in data breaches. With strong 3D Liveness & 3D Matching, 2D photos stored online (or breached) can’t be leveraged against your users. Whitepaper
- Delete Liveness Data after each login and collect new Liveness Data for every new session. This prevents biometric honeypots and allows for safe, centralized biometric storage. See www.Liveness.com
- You store all of your User’s biometric data & PII on your servers which run FaceTec’s software inside your firewall. 3D is the only way to verify biometric identity remotely, enable cross-platform logins, simplify device upgrades, & allow multiple users /device.
- Only true 3D Algorithms that measure the shape of the user’s face can be unbiased to skin tone. FaceTec trained its 3D Algorithms with the help of over half-a-million volunteer testers from over 180 countries.
- Get the Acuity Research Report: Face Verification & Liveness Synonymous with Remote Onboarding








